Canon相機收購,二手收購,收購相機,全新相機,二手相機 收購5D Mark IV,收購EOS-1D X Mark II,收購EOS M3/M10 收購canon canon 5Ds/5Ds R,,5D Mark III/6D II,7D Mark II 70D/80D,750D/760D,700D/100D 收購FUJIFILM 相機,全系列FUJIFILM 收購二手Nikon 相機,Nikon二手收購,全新Nikong買賣 D3400收購 Nikon 1 j5收購 D750 Df/D810/D610,D5/D4S,D500,D7200/D7500,D5500/D5300 OLYMPUS
標籤: canon相機收購
Canon’s flagship DSLR line will end with the EOS-1D X Mark III, eventually canon相機收購
canon相機收購
canon相機收購canon’s flagship DSLR line will end with the EOS-1D X Mark III, eventually
canon相機收購canon’s flagship DSLR line will end with the EOS-1D X Mark III, eventually
/
In the next few years, canon相機收購canon will end development and production of its top-of-the-line DSLR camera
Share this story
When canon相機收購canon revealed the EOS-1D X Mark III in January 2020, we proclaimed that the DSLR “still isn’t dead,” but that camera will mark the end of the line for a flagship model that some pro photographers still swear by to capture everything from sporting events to wild animals.
An end to the production and development timeline of the EOS-1 is estimated as “within a few years.”
canon相機收購canonRumors points out an interview canon相機收購canon’s chairman and CEO Fujio Mitarai gave this week to the Japanese newspaper Yomiuri Shimbun (via Y.M. Cinema Magazine). The piece highlight how high-end mirrorless interchangeable-lens cameras have taken market share digital single-lens reflex (DSLR) cameras previously dominated.
In it, the CEO is quoted (in Japanese, which we’ve translated to English) saying “Market needs are rapidly moving toward mirrorless cameras. So accordingly, we’re increasingly moving people in that direction.” The article states that the Mark III is “in fact” the last model in canon相機收購canon’s flagship EOS-1 series and that in a few years canon相機收購canon will stop developing and producing its flagship DSLR cameras in favor of mirrorless cameras.
However, despite what some headlines say, it doesn’t mean this is the end of canon相機收購canon DSLRs (yet). While the article makes it plain that mirrorless cameras like canon相機收購canon’s own EOS R3 represent the future of the segment, it also says that because of strong overseas demand, the company plans to continue making intro/mid-range DSLR cameras for the time being.
As for the Mark III itself, while a new model is not around the corner, its estimated lifespan as an active product is still measured in years. In a statement given to The Verge, a canon相機收購canon US spokesperson confirmed, “The broad details of Mr. Mitarai’s interview as described in the article are true. However, while estimated as “within a few years,” exact dates are not confirmed for the conclusion of development/termination of production for a flagship DSLR camera.”
 (圖/翻攝 canon相機收購canon官網)
(圖/翻攝 canon相機收購canon官網)
canon相機收購canon 終於掀開底牌!自從推出 EOS R 系統以來,外界都在好奇 canon相機收購canon 何時推出最頂級型號代表的 EOS R1?今日(15)官方證實,這款頂級機皇將於 2024 年正式發佈,搭載新技術的影像加速處理器、對焦系統。
根據 canon相機收購canon 說法,EOS R1 將是一款面向運動攝影、新聞報導、影音製作的專業級全片幅無反相機,結合頂級性能、可靠性以及耐用於一身。除了現有的 DIGIC X 影像處理器,會再加入全新的 DIGIC Accelerator 影像加速處理器,能夠在短時間內處理大量數據,有利於自動對焦的效能提升。
此外,canon相機收購canon 將透過深度學習,實現更快、準度更精確的主體辨識,在運動賽事中,就算想要拍攝的球員被其他球員擋住,後續也能對焦追蹤,並且自動對焦會帶來「動作優先」功能,將能分析主體的移動方向,像是當籃球員準備投籃的時候,能夠提早預測,立即轉移對焦點捕捉關鍵畫面。
canon相機收購canon 表示,EOS R1 已經正在進行實機測試,將在未來舉辦的國際體育賽事捕捉決定性的瞬間,暗示相機或有望在夏季巴黎奧運會之前亮相。
canon相機收購 canon相機收購
Sony 旗艦單眼 α9 III 在台上市!首搭全域快門締 120fps 高速連拍 canon相機收購
canon相機收購
 (圖/記者黃肇祥攝)
(圖/記者黃肇祥攝)
Sony 今日(17)在台上市全片幅無反單眼相機 α9 III,搭載業界首款「全域快門」全片幅感光元件,締造高達 120fps 高速連拍,並且拍出無變形、無黑屏的照片。
α9 III 採用內建額外記憶體的 2460 萬畫素全片幅感光元件,具備機身 8.0 級 5 軸光學影像穩定系統,能拍攝 4K 120p 無裁切影片,瞄準專業攝影師,尤其是考驗高速連拍的運動、生態攝影領域。最大亮點是全域快門,以往只出現於 1 吋以下的隨身相機,或是不講究畫質的工業相機,α9 III 為第一款把該規格引入全片幅感光元件的單眼相機,得以兼顧高速連拍與高畫質。
全域快門的差異是什麼呢?Sony 亞太區技術產品經理藤本祐介解釋,有別於傳統滾動式快門由上至下讀取像素,照片與照片存在一定的等待時間,全域快門能一次同時讀取所有像素,能夠避免以前高速連拍常見的果凍效益、黑屏畫面。
 α9 III 實拍。全域快門一次讀取所有像素,因此能避免果凍效益,高速揮動的球桿不會因為逐行掃描而出現變形、歪斜。(圖/記者黃肇祥攝)
α9 III 實拍。全域快門一次讀取所有像素,因此能避免果凍效益,高速揮動的球桿不會因為逐行掃描而出現變形、歪斜。(圖/記者黃肇祥攝) α9 III 搭配支援閃光燈,能以 1/80000 秒的速度與閃光燈同步拍攝,更輕易捕捉每一瞬間的畫面。(圖/記者黃肇祥攝)
α9 III 搭配支援閃光燈,能以 1/80000 秒的速度與閃光燈同步拍攝,更輕易捕捉每一瞬間的畫面。(圖/記者黃肇祥攝) (圖/記者黃肇祥攝)
(圖/記者黃肇祥攝) 「預拍功能」能提前一秒以Raw格式拍攝,左上角有箭頭的標示,就是以「預拍功能」功能拍攝的照片。(圖/記者黃肇祥攝)
「預拍功能」能提前一秒以Raw格式拍攝,左上角有箭頭的標示,就是以「預拍功能」功能拍攝的照片。(圖/記者黃肇祥攝)
之所以能達成全域快門,Sony 依靠的是新一代 Bionz XR 影像處理器,在 120fps 連拍之中能確保每一張都有自動對焦與自動曝光,並且搭配覆蓋率 95.6%、多達 759 個相位式自動偵測對焦點,以及 AI 處理元件能持續鎖定拍攝的主題的型態、動作以及眼部對焦,不會因為其他物體忽然穿插於前景而改變焦點。
Sony 這次在 α9 III 首度帶來兩項輔助功能,首先是「預拍功能」,可以藉由感光元件的暫存記憶體,在釋放快門前 1 秒提早開始捕捉畫面,減少錯失精采畫面的遺憾。此外,還有能藉由自訂按鍵瞬間啟用的「連拍加速功能」,可暫時提高拍攝速度,省去手動調整參數的步驟。
 (圖/記者黃肇祥攝)
(圖/記者黃肇祥攝)
Sony α9 III 預計於 1 月 19 日在台開賣,售價為 184,980 元,搭配的垂直拍攝手把 VG-C5 售價是 12,980 元。同日登場的還有 EF 300m F2.8 GM OSS 望遠大光圈鏡頭,有同級最輕巧的 1,470g 鏡身,售價 194,980 元,從今日起開放訂購。
 (圖/翻攝canon相機收購canon官網)
(圖/翻攝canon相機收購canon官網)
一年一度由日本相機工業協會正式評選的「最具歷史性相機」,正式公佈 2023 年獲選的 4 大機款,不只是比技術的創新,更有像是 canon相機收購canon 以划算的入門價格獲得肯定。
「最具歷史性相機」主要聚焦於日本相機品牌,每年都會選出最具有代表性的產品,可能是技術創新,又或者是最受歡迎,被視為有一定歷史定位的相機。今年入選的分別為 canon相機收購canon EOS R100、Nikon Zf、Pentax K-3 Mark III Monochrome 及 Sony 發佈的DSC-HX99 RNV Kit 視網膜投影相機組。
日本相機工業協會針對每一款機型列出入選原因,像是 canon相機收購canon EOS R100 就是出自於它的平價,單機身僅需 480 美元(約 14,997 元),可惜尚未於台灣上市。Nikon Zf 則不只是有高顏值,最具意義的是在無反相機內,首度加入連結對焦點功能,帶來 8.0 級防手震的 VR 模組。
Sony 旗下的 DSC-HX99 RNV Kit 視網膜投影相機組,則是一款瞄準特殊用途的相機,藉由雷射是網膜投影技術,讓視力受損的民眾也能享受拍照樂趣。專攻黑白照片的 Pentax K-3 Mark III Monochrome,則是首款採用單色專用感光元件的單反相機。
canon相機收購 canon相機收購
Canon’s new dual-fisheye EOS R lens is for creating 3D VR content canon相機收購
canon相機收購
canon相機收購canon’s new dual-fisheye EOS R lens is for creating 3D VR content
canon相機收購canon’s new dual-fisheye EOS R lens is for creating 3D VR content
/
It’ll be out in December for $1,999
Share this story
canon相機收購canon has announced what’s easily the oddest glass yet for its EOS R mirrorless camera system: a dual 5.2mm f/2.8 fisheye. The fisheye lenses are 60mm apart and are designed for creating 3D VR images and video content; canon相機收購canon calls out the Oculus Quest 2 as a potential hardware destination and says this is “the world’s first digital interchangeable lens that can capture stereoscopic 3D 180° VR imagery to a single image sensor.”
The lens can be used to shoot up to 8K footage on the EOS R5, which appears to be the only camera it’ll work with. canon相機收購canon is releasing a 1.5.0 firmware update for the R5 as well as a Premiere Pro plug-in and a standalone file conversion app called EOS VR Utility. canon相機收購canon calls this combination the EOS VR System and will be making the software available on a subscription basis.
The lens will cost $1,999, while the EOS R5 sells for $3,899. That’s a pricey combination, but not too much more than some dedicated VR cameras like the Insta360 Pro 2, and canon相機收購canon’s solution should be a lot more versatile. The lens and software will both be released in December.

▲canon相機收購canon EOS R 系統邁五週年。(圖/canon相機收購canon提供)
記者樓菀玲/綜合報導
canon相機收購canon 於「2023 年台北攝影器材展暨影音創作設備展」盛大亮相,全新主題「完美光學再定義」為消費者呈現其最新的數位相機、印表機和專業攝影機,更宣布即日起提供 RF 系列鏡頭三年保固服務,引發愛好者暴動。
此外,為慶祝 EOS R 系統五週年,canon相機收購canon 消費性產品事業群副總高耀聰公布,從即日起 canon相機收購canon 在台灣提供 RF 系列鏡頭三年保固,這不僅證明了 canon相機收購canon 對其產品的自信,更是對消費者的誠心承諾。
展覽期間,canon相機收購canon 也安排了豐富的攝影講座,共24場,涵蓋各式主題,為攝影愛好者和影音創作者提供專業知識。現場參與者更有機會參與各式活動,並有機會獲得 CP1500 印相機等大獎。特別的促銷優惠和限時活動等眾多好康,絕對值得一遊。
canon相機收購canon 的展區不僅專注於相機,其印表機部分也大放異彩。特色的 PRO 系列 A3+ 專業相片印表機和 G 系列大供墨複合機都能夠精確列印出高品質的照片,給予消費者最佳的視覺饗宴。專業攝影機部分更展出了完整的數位錄影機、電影級機種和鏡頭系列,讓影音創作者大開眼界。
canon相機收購 canon相機收購
手機打字恐暴露年紀!達人觀察:超過 65 歲才會用到這一指 canon相機收購
canon相機收購
 (圖/美聯社)
(圖/美聯社)
用手機打字的時候,你主要用哪一根手指頭呢?近期一名 TikTok 創作者實際觀察,發現各個年齡層均有截然不同的打字習慣,甚至能作為世代的判斷方式,影片發布後引起廣大網友關注。
經常分享 3C 技巧的創作者 Tyler Morgan 於最新影片指出,透過觀察自己同事、朋友,發現手機打字的方式與年齡有大的關聯,例如千禧年世代(出生於 1981~1996 年之間)通常會是兩隻手的拇指,或是以單手滑動為主。若是更為年輕的 Z 世代(出生於 1997~2012 年之間)方法與千禧年一樣,只是速度會更快一些。
到了出生於 1965~1980 年的 X 世代,會開始混用拇指與食指,可能一隻手支撐,另一隻手透過食指點擊。至於年紀稍長的 1946~1964 年出生的嬰兒潮世代,則會完全仰賴單一食指點擊的方式。
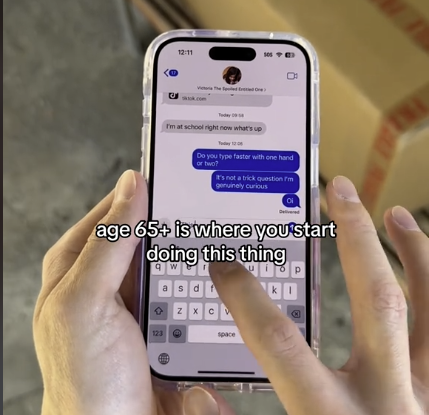 Tyler Morgan 發現,超過 65 歲的人較習慣以單指點擊的方式。(圖/翻攝 Tyler Morgan TikTok 影片)
Tyler Morgan 發現,超過 65 歲的人較習慣以單指點擊的方式。(圖/翻攝 Tyler Morgan TikTok 影片)
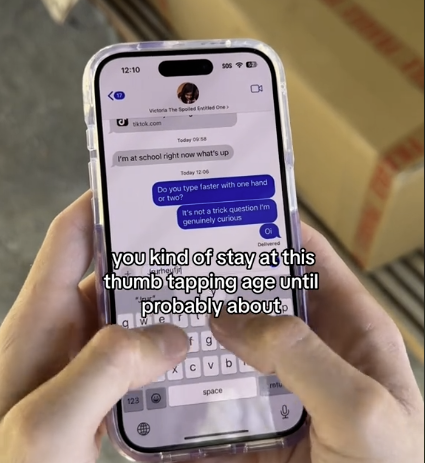 目前多數人都採用兩手拇指來打字。(圖/翻攝 Tyler Morgan TikTok 影片)
目前多數人都採用兩手拇指來打字。(圖/翻攝 Tyler Morgan TikTok 影片)
Tyler Morgan 認為,之所以有如此改變,可能是因為隨著年紀增長,我們身體機能逐漸下滑,對於十幾、二十歲用戶很輕鬆的事情,到了六十歲不見得能感覺一樣舒適自在。
影片發出之後,引發超過 14 萬人給予愛心,並且累積超過 8,000 則回覆,也有人分享,現在長輩不一定會打字,通常只用語音轉文字,也有網友分享,現在手機太大,已經沒有辦法舒服地用拇指打字。

▲ canon相機收購canon RF10-20mm F4 L IS STM 在台開賣。(圖/翻攝自 canon相機收購canon)
記者樓菀玲/台北報導
canon相機收購canon 世界首支 10mm 超廣角全片幅自動對焦鏡頭 RF10-20mm F4 L IS STM,即日起在台正式開賣,輕盈小巧的設計,長度僅約 11.2 公分及重量僅約 570 公克,並提供10mm-20mm 超廣角變焦範圍,輕鬆將廣闊視野盡收眼底。
據了解,鏡頭內建光學影像穩定器,除了提供 5 級防手震效果外,更首次加入周邊協調控制(Peripheral Coordinated Control),配合機身防手震時能有效校正廣角鏡頭經常出現的周邊震動模糊,讓相片的周邊可有更高的影像畫質,拍攝短片時亦可以減低畫面周邊的輕微震動。
基於 RF10-20mm F4 L IS USM 是世界首支 10mm 超廣角全片幅自動對焦鏡頭,能夠帶來 130° 25’ 超廣角視角,廣角鏡頭的廣角端焦距即便相差 1mm ,拍攝範圍也有很大差距。
而 10mm 焦距可涵蓋的畫面面積約為 14mm 的 2 倍、約為 12mm 的 1.4 倍,極其廣闊的視角讓鏡頭適用於狹小空間的拍攝,也可以拍攝整體建築物、廣闊的風景、頭頂上的星空等主題。

▲ 10mm 廣角端可以收錄更多內容在畫面中,圖為攝影熱點東北角十三層遺址。(圖/翻攝自 canon相機收購canon)
從帳面規格來看,RF10-20mm F4 L IS USM 的重量為 570 公克,而長度僅約 11.2 公分,整體設計更加便於攜帶,機動性加倍,無論手持或加入穩定器移動拍攝皆非常適合。
鏡頭本身採用 canon相機收購canon 全新研發的 12 組 16 片光學設計,充分發揮 RF 接環大口徑與短後對焦距離的優勢,這光學設計是在採用相機內建數位變形校正的前題下提升整體影像品質,並為畫面邊緣範圍提供清晰描寫能力。
canon相機收購 canon相機收購
Canon EOS R7 單機身 公司貨 canon相機收購
特約記者洪聖壹/綜合報導
SONY 公司這兩年真的是大爆發,針對中階用戶推出 A7III、A7RIV,還推出所謂「網紅機」ZV-1,在昨晚可說是毫無保留,以「前所未見(The One Never Seen)」為名,推出全片幅無反相機 α1(A1,英文名稱Alpha One),以數字來看,就是 5010 萬畫素、15 級動態範圍、30fps 連拍、8K 拍攝,售價來到 6500 美元(約台幣 18.2 萬元)。

去年夏天,canon相機收購canon 公司推出的 EOS R5,搭載全球首部 8K,4,500 萬畫素全幅 CMOS 感光元件,支援無裁切、最高 120p 4K 的短片拍攝,高達 8 級機身五軸防震能力,最高 20fps 連續拍攝,被稱為該公司革新機種。
如今時隔半年不到,Sony 公司立刻還以顏色,以 “The One”Never Seen 為名,推出的 SONY α1 能夠以更高的 5,010 萬畫素,每秒鐘連續拍攝 30 張照片,並且可以透過連續拍攝 16 張照片組合成一張 1 億 9900 萬畫素照片,側邊還具備雙 SD UHS II、雙CFexpress 卡槽以即時存取內容。

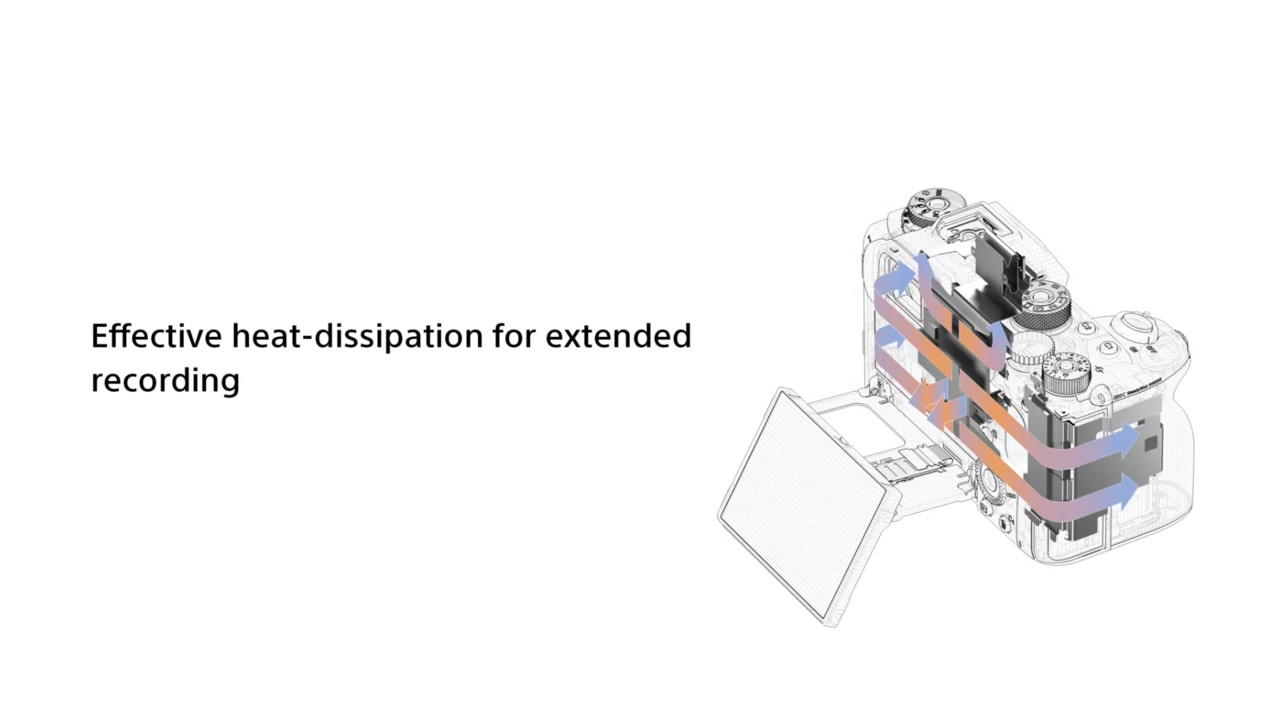
SONY α1 的數位觀景窗使用跟 α7SIII 相同的 944 萬液晶螢幕,可以做到更精細的每秒 240 次更新,並且把 8K@30P、4K@120P 的高規格拍攝能力也塞入 α1,全機身採用多重環繞式散熱系統與 5.5 級 5 軸防手震設計,讓相機即使邊走邊拍 4K、8K 影片 30 分鐘不只維持很好的拍攝品質、而且不過熱。


SONY α1 支援人眼對焦,拍攝對焦點來到 759 點、覆蓋範圍高達 92%,並且支援 4:2:2 10bit 色彩取樣、16bit RAW、SLog-3 或 HLG 輸出,同時也擁有旗艦機才有的 S-Cinetone 功能。
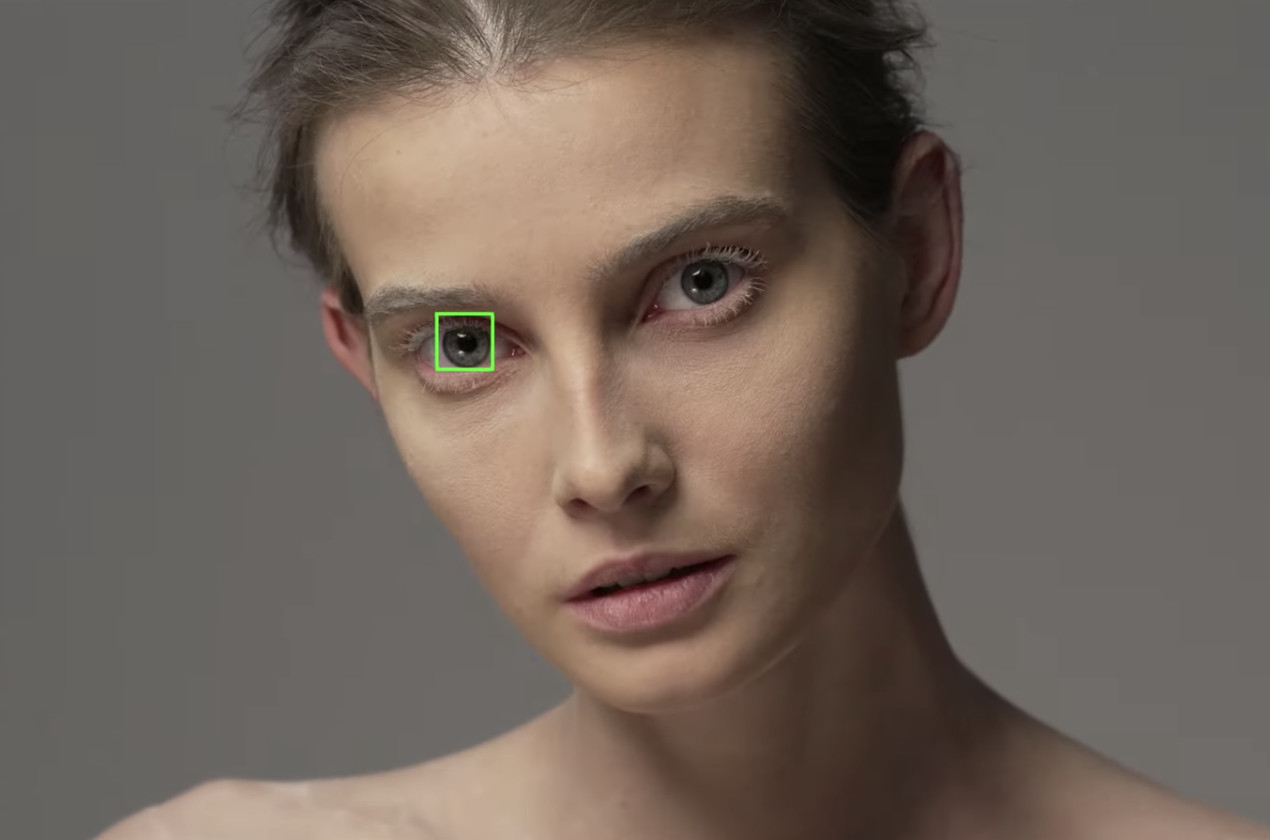
在影音輸出方面,SONY α1 側邊有 HDMI 孔支援 16-bit RAW 輸出,而且還多了 USB 3.2 Type-C (10Gbps) 孔、多了一個 1000BASE-T LAN 網路連接能力、內建 2×2 MIMO AC 無線傳檔、FTP 連線,透過各種形式,傳輸高品質影音內容,提升工作效率,舉例來說,消費者可以直接用 USB-C 連接 SONY Xperia 1 II 5G 手機,快速將存取好的照片,進行機上修圖,然後上傳到社群平台,從數位相機的演變進程來看,這可以說是一個里程碑。
SONY α1 機身重量只有 737 克,售價約 6500 美元,折合台幣約 18.2 萬元,下面有幾個代表性的拍攝樣張,提供給讀者參考:



canon相機收購 canon相機收購
Canon cameras can now automatically upload your pictures to Google Photos canon相機收購
canon相機收購
canon相機收購canon cameras can now automatically upload your pictures to Google Photos
canon相機收購canon cameras can now automatically upload your pictures to Google Photos
/
But you need a Google One membership
Share this story
Google are making it easier to move images from your camera to Google Photos. Owners of recent canon相機收購canon cameras can now automatically upload photos and videos to the popular photo management platform by wirelessly slinging them via your phone.
This auto-backup to Google Photos feature works with both the iOS and Android versions of the image.canon相機收購canon app, but you’ve got to make sure your camera is compatible. If it is, just make sure you’ve got the latest image.canon相機收購canon app update installed and you’ll see the new option for transferring photos to Google Photos. After activating the new feature in canon相機收購canon’s app, future photos and videos will be sent automatically to Google’s photo storage platform. You don’t have to worry about losing any quality from your shots, either: all images are synced to Google Photos at their original quality.
In February, canon相機收購canon launched its own version of a cloud backup service, image.canon相機收購canon, which similarly allows canon相機收購canon cameras to seamlessly back up photos over Wi-Fi. From image.canon相機收購canon, users have the option of automatically transferring their images and videos to other places, such as Google Drive or YouTube (for uploaded videos), and now Google Photos has been added to that list.
Your photos go to canon相機收購canon’s cloud backup service, too
But there is one asterisk here that might irk some people: a Google One membership is required to transfer your photos this way. Google is offering canon相機收購canon customers a one-month trial to Google One (with 100GB of storage) to help ease them into the service. Once the trial is up, Google One plans start at $2 per month for 100GB of storage.
Earlier this month, canon相機收購canon temporarily suspended image.canon相機收購canon after some stored photos and videos went missing. So far — knock on wood — Google Photos hasn’t encountered any such issues.
Update, 6:43 PM ET: Clarified that technically, these images aren’t being sent directly from your camera to the cloud — they’re being routed through your phone.
 (圖/翻攝canon相機收購canon官網)
(圖/翻攝canon相機收購canon官網)
一年一度由日本相機工業協會正式評選的「最具歷史性相機」,正式公佈 2023 年獲選的 4 大機款,不只是比技術的創新,更有像是 canon相機收購canon 以划算的入門價格獲得肯定。
「最具歷史性相機」主要聚焦於日本相機品牌,每年都會選出最具有代表性的產品,可能是技術創新,又或者是最受歡迎,被視為有一定歷史定位的相機。今年入選的分別為 canon相機收購canon EOS R100、Nikon Zf、Pentax K-3 Mark III Monochrome 及 Sony 發佈的DSC-HX99 RNV Kit 視網膜投影相機組。
日本相機工業協會針對每一款機型列出入選原因,像是 canon相機收購canon EOS R100 就是出自於它的平價,單機身僅需 480 美元(約 14,997 元),可惜尚未於台灣上市。Nikon Zf 則不只是有高顏值,最具意義的是在無反相機內,首度加入連結對焦點功能,帶來 8.0 級防手震的 VR 模組。
Sony 旗下的 DSC-HX99 RNV Kit 視網膜投影相機組,則是一款瞄準特殊用途的相機,藉由雷射是網膜投影技術,讓視力受損的民眾也能享受拍照樂趣。專攻黑白照片的 Pentax K-3 Mark III Monochrome,則是首款採用單色專用感光元件的單反相機。
canon相機收購 canon相機收購
These Canon cameras are secretly Robots in Disguise canon相機收購
canon相機收購
These canon相機收購canon cameras are secretly Robots in Disguise
These canon相機收購canon cameras are secretly Robots in Disguise
/
Surprise! They’re Transformers
Share this story
Don’t you just hate it when you pick up your trusty canon相機收購canon EOS R5, only to discover it’s actually a sneaky Transformer? Well bad news, because this nightmarish future spotted by TFormers is actually becoming a reality next year thanks to a collaboration between Takara Tomy (the Japanese company behind the Transformers toys) and canon相機收購canon (the Japanese company behind… well you get the idea).
The collaboration has resulted in a pair of Transformers figurines that are able to fold away into surprisingly realistic looking canon相機收購canon mirrorless cameras. I say “surprisingly realistic” because at first glance I somehow mistook these for functioning cameras. But in case it wasn’t obvious from their ¥ 19,800 (around $147) pricing, they’re non-functional replicas that are only 80-percent of the size of the real thing. (The idea that this could be a functioning camera isn’t so wild considering Takara Tomy has previously produced working MP3-player Transformer toys).
Probably my favorite detail is the lens cap, which in both cases transform into shields for the Transformers to wield. But a close second is the miniature cameras both figurines appear to be holding in some of the promotional images, which is a delightfully silly addition. One figurine is based on Optimus Prime, while the other is Decepticon Refraktor.
Both Transformers are scheduled to release in Japan next year on February 25th, and TFW2005 reports that preorders are open from now until September 28th. It’s unclear if they’ll see a global release.
 (圖/彭博社)
(圖/彭博社)
蘋果於二月開賣首款空間運算裝置 Vision Pro,開啟虛擬頭盔的軍備競賽!業界領頭羊 Meta 近期傳出,正在籌備一款比現有 Quest 3 更平價的新機型,至於 HTC 則打出業界最大方的分潤比例,要積極拉攏開發者。
有網友在 X 平台釋出疑似 Meta 的官方簡報,透露即將發表「Meta Quest 3S」頭盔,定位將是介於 Quest 3、Quest 2 兩代產品之間,外型上較顯著的差異是在鏡頭感應器的部分,從 Quest 3 的三條橫槓,變成兩邊各三顆圓點。
從流出的簡報也能證實,Quest 3S 解析度將會略低於 Quest 3,落在 1832×1020、20ppd,是與 Quest 2 同級,並也提供 128GB、256GB 儲存空間。根據先前外媒爆料指出,Quest 3S 有望採用與 Quest 3 相同的 Snapdragon XR2 Gen 3 晶片,帶來比 Quest 2 更流暢的體驗,主要是在畫質上相對犧牲一些。
日前 Meta 就曾向外媒《The Verge》證實,今年會推出一款代號為「Ventura」的評價頭盔,目標是在 VR 的消費市場提供最吸引力的價格,這款產品有望是本次流出的 Quest 3S。
至於 HTC 則是著手於調整內容收益分潤率政策,宣布從 4 月 1 日起,所有上架至旗下 XR 應用商店、VIVEPORT 的 VR 內容,開發者將能獲得一次性購買遊戲和應用內容 90% 的收益,代表平台只從中收取 10%。比起其他平台慣例收取 30% 或更高的抽成,低上不少。
HTC 表示,此舉是為了促進 XR 生態發展,讓開發者能在 VIVEPORT 平台獲得更高比例的收益,有助推動整個產業的發展和創新。
canon相機收購 canon相機收購
These Canon cameras are secretly Robots in Disguise canon相機收購
canon相機收購
These canon相機收購canon cameras are secretly Robots in Disguise
These canon相機收購canon cameras are secretly Robots in Disguise
/
Surprise! They’re Transformers
Share this story
Don’t you just hate it when you pick up your trusty canon相機收購canon EOS R5, only to discover it’s actually a sneaky Transformer? Well bad news, because this nightmarish future spotted by TFormers is actually becoming a reality next year thanks to a collaboration between Takara Tomy (the Japanese company behind the Transformers toys) and canon相機收購canon (the Japanese company behind… well you get the idea).
The collaboration has resulted in a pair of Transformers figurines that are able to fold away into surprisingly realistic looking canon相機收購canon mirrorless cameras. I say “surprisingly realistic” because at first glance I somehow mistook these for functioning cameras. But in case it wasn’t obvious from their ¥ 19,800 (around $147) pricing, they’re non-functional replicas that are only 80-percent of the size of the real thing. (The idea that this could be a functioning camera isn’t so wild considering Takara Tomy has previously produced working MP3-player Transformer toys).
Probably my favorite detail is the lens cap, which in both cases transform into shields for the Transformers to wield. But a close second is the miniature cameras both figurines appear to be holding in some of the promotional images, which is a delightfully silly addition. One figurine is based on Optimus Prime, while the other is Decepticon Refraktor.
Both Transformers are scheduled to release in Japan next year on February 25th, and TFW2005 reports that preorders are open from now until September 28th. It’s unclear if they’ll see a global release.
特約記者洪聖壹/綜合報導
SONY 公司這兩年真的是大爆發,針對中階用戶推出 A7III、A7RIV,還推出所謂「網紅機」ZV-1,在昨晚可說是毫無保留,以「前所未見(The One Never Seen)」為名,推出全片幅無反相機 α1(A1,英文名稱Alpha One),以數字來看,就是 5010 萬畫素、15 級動態範圍、30fps 連拍、8K 拍攝,售價來到 6500 美元(約台幣 18.2 萬元)。

去年夏天,canon相機收購canon 公司推出的 EOS R5,搭載全球首部 8K,4,500 萬畫素全幅 CMOS 感光元件,支援無裁切、最高 120p 4K 的短片拍攝,高達 8 級機身五軸防震能力,最高 20fps 連續拍攝,被稱為該公司革新機種。
如今時隔半年不到,Sony 公司立刻還以顏色,以 “The One”Never Seen 為名,推出的 SONY α1 能夠以更高的 5,010 萬畫素,每秒鐘連續拍攝 30 張照片,並且可以透過連續拍攝 16 張照片組合成一張 1 億 9900 萬畫素照片,側邊還具備雙 SD UHS II、雙CFexpress 卡槽以即時存取內容。

SONY α1 的數位觀景窗使用跟 α7SIII 相同的 944 萬液晶螢幕,可以做到更精細的每秒 240 次更新,並且把 8K@30P、4K@120P 的高規格拍攝能力也塞入 α1,全機身採用多重環繞式散熱系統與 5.5 級 5 軸防手震設計,讓相機即使邊走邊拍 4K、8K 影片 30 分鐘不只維持很好的拍攝品質、而且不過熱。



SONY α1 支援人眼對焦,拍攝對焦點來到 759 點、覆蓋範圍高達 92%,並且支援 4:2:2 10bit 色彩取樣、16bit RAW、SLog-3 或 HLG 輸出,同時也擁有旗艦機才有的 S-Cinetone 功能。


在影音輸出方面,SONY α1 側邊有 HDMI 孔支援 16-bit RAW 輸出,而且還多了 USB 3.2 Type-C (10Gbps) 孔、多了一個 1000BASE-T LAN 網路連接能力、內建 2×2 MIMO AC 無線傳檔、FTP 連線,透過各種形式,傳輸高品質影音內容,提升工作效率,舉例來說,消費者可以直接用 USB-C 連接 SONY Xperia 1 II 5G 手機,快速將存取好的照片,進行機上修圖,然後上傳到社群平台,從數位相機的演變進程來看,這可以說是一個里程碑。
SONY α1 機身重量只有 737 克,售價約 6500 美元,折合台幣約 18.2 萬元,下面有幾個代表性的拍攝樣張,提供給讀者參考:



canon相機收購 canon相機收購
Canon EOS 90D 單機身 公司貨 canon相機收購
 (圖/翻攝canon相機收購canon官網)
(圖/翻攝canon相機收購canon官網)
一年一度由日本相機工業協會正式評選的「最具歷史性相機」,正式公佈 2023 年獲選的 4 大機款,不只是比技術的創新,更有像是 canon相機收購canon 以划算的入門價格獲得肯定。
「最具歷史性相機」主要聚焦於日本相機品牌,每年都會選出最具有代表性的產品,可能是技術創新,又或者是最受歡迎,被視為有一定歷史定位的相機。今年入選的分別為 canon相機收購canon EOS R100、Nikon Zf、Pentax K-3 Mark III Monochrome 及 Sony 發佈的DSC-HX99 RNV Kit 視網膜投影相機組。
日本相機工業協會針對每一款機型列出入選原因,像是 canon相機收購canon EOS R100 就是出自於它的平價,單機身僅需 480 美元(約 14,997 元),可惜尚未於台灣上市。Nikon Zf 則不只是有高顏值,最具意義的是在無反相機內,首度加入連結對焦點功能,帶來 8.0 級防手震的 VR 模組。
Sony 旗下的 DSC-HX99 RNV Kit 視網膜投影相機組,則是一款瞄準特殊用途的相機,藉由雷射是網膜投影技術,讓視力受損的民眾也能享受拍照樂趣。專攻黑白照片的 Pentax K-3 Mark III Monochrome,則是首款採用單色專用感光元件的單反相機。
canon相機收購 canon相機收購
Canon EOS 90D BODY (公司貨) canon相機收購

▲ canon相機收購canon 新一代入門無反相機 EOS R8。(圖/翻攝自 canon相機收購canon 官網)
記者樓菀玲/台北報導
canon相機收購canon EOS R8 全片幅無反光鏡相機今日正式上市,為 canon相機收購canon 旗下最經濟型機種,為 EOS RP 後繼機種,可為首次購買全片幅相機的攝影愛好者及內容創作者提供卓越性能,號稱同價位機型當中最強規格的無反相機。
今日,canon相機收購canon 正式推出全新全片幅無反光鏡相機 EOS R8,該相機以輕量化機身和先進的功能吸引攝影愛好者和內容創作者,機身僅重 461 克,具備 2,420 萬像素全片幅 CMOS 影像感測器,並提供 6K 超取樣 4K 60p、FHD 180p 錄影功能以及 canon相機收購canon Log 3。此外,該相機還配備電子快門,最高可達 40 FPS 連拍。
對於創作者而言,EOS R8 具有無與倫比的錄影和拍照功能,可利用 6K RGB 素材超取樣的無裁切 4K UHD 60p 錄影功能來創作,實現高畫質和細緻的短片表現。而且,EOS R8 可連續拍攝 30 分鐘或以上的無裁切 4K UHD(6K超取樣)60p 短片。
為了滿足各種拍攝需求,EOS R8 支援 8-bit 及 YCbCr 4:2:2 10-bit 短片選項、canon相機收購canon Log 3 和 HDR PQ。10-bit HDR PQ 能在無需後期調色的情況下錄製高亮度、豐富層次和廣色域的短片。此外,EOS R8 還具有偽色顯示、斑馬紋顯示、呼吸效應補償功能以及 5 軸防震的短片數位 IS。

▲ EOS R8 。(圖/翻攝自 canon相機收購canon 官網)
在設計方面,EOS R8 的按鈕重新設計,以提高拍攝操作性。機身左肩加入相片/短片模式切換開關,方便快速轉換拍攝模式。此外,視覺指南可以幫助新手輕鬆掌握相機的功能和設定。
該相機配備了高精度電子觀景器,提供 0.39 吋 236 萬點 0.7 倍 OLED 顯示,最高可達 120FPS。此外,還具有多角度觸控螢幕和防塵防水滴設計,使攝影過程更加便捷與靈活。
總之,canon相機收購canon EOS R8 以其輕巧的機身、卓越的性能和專業功能成為攝影愛好者和內容創作者的理想選擇,配有光學影像穩定器的 RF/RF-S 鏡頭與 EOS R8 的數位防震功能相結合,可實現更穩定流暢的影片效果。此外,OVF 模擬顯示輔助功能通過HDR技術提供更自然的高光和暗部漸變,重現傳統單眼相機光學觀景窗畫面。
高度靈活的 3 吋 162 萬點多角度 Clear View II LCD 觸控螢幕,讓攝影師能夠在高、低角度或繞過障礙物拍攝時尋找新的視角。此外,EOS R8 採用輕巧鎂合金機架加強耐用度,防塵防水滴設計則有助於防止灰塵和水滴滲入相機,目前已知 canon相機收購canon EOS R8 在台售價為 43,900 元,搭配 RF24-50mm f/4.5-6.3 IS STM 鏡頭的 KIT 組合則是為 49,900 元。
canon相機收購 canon相機收購

:format(webp)/cdn.vox-cdn.com/uploads/chorus_asset/file/19580266/1DXbody_3Q_hiRes.jpg)

:format(webp)/cdn.vox-cdn.com/uploads/chorus_asset/file/13707075/akrales_190117_3163_0194.jpg)

